If you’ve been following the news, you would have come across a term called Ransomware. It is a type of computer virus which uses encryption as a weapon for destruction rather than protection of data. It encrypts files on an infected system and then demands a ransom, from the user of the infected machine, to decrypt the files.
Here’s how it works:
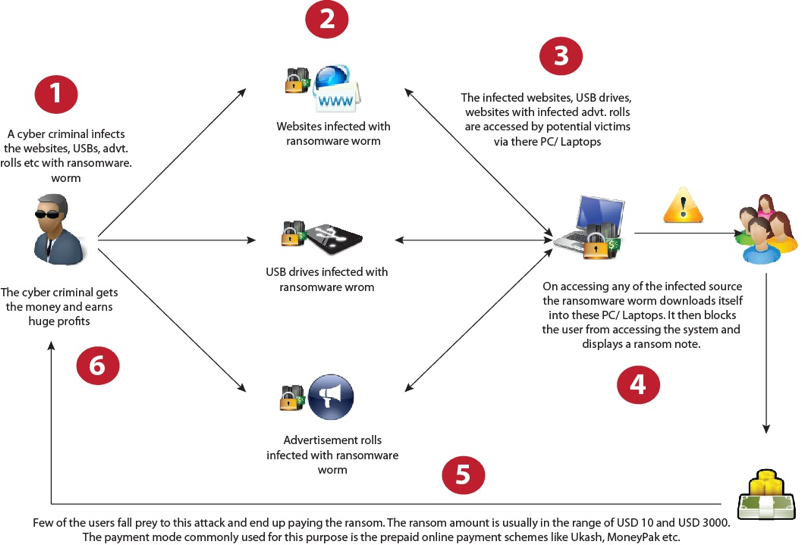
The popularity of ransomware has made it a new poster boy of cyber threats. Apart from computers, news and security conferences, it has recently made it’s television debut in a US television show titled, Mr. Robot.
“Mr. Robot follows Elliot, a young programmer who works as a cyber-security engineer by day and a vigilante hacker by night. Elliot finds himself at a crossroads when the mysterious leader of an underground hacker group recruits him to destroy the corporation he is paid to protect.”
The first episode of the second season has recently aired. Among other things (and without giving more spoilers) it shows how the hacker group, fsociety, uses CryptoWall, a popular ransomware, to bring down a bank’s IT infrastructure.
One thing that makes Mr. Robot a must watch for cyber security folks is the level of detailing. Gone are the days when green text on a black terminal and some random commands (or text) were used to depict the activity of hacking. Mr. Robot uses real-world tools such as Metasploit, nmap, netcat etc. For instance, in this episode Darlene (Carly Chaikin) uses the Social Engineering Toolkit module of Metasploit to create a USB drive consisting CryptoWall ransomware. Here’s a screenshot of commands given by her:

Through these commands she’s creating a social engineering attack with CryptoWall as it’s payload. In the first two commands (start counting after set:modules > 1), she specifies the IP address and port number of the target machine. The third command instructs the payload to launch a recursive (repeated) attack on all computers in the network. In next two commands she assigns a name to the payload and enters the passphrase for it. In the last command, she creates an autorun.inf file which would automatically execute the payload when the USB drive is plugged into the machine.
Upon completion, she hands over this USB drive to Mobley (Azhar Khan) who then social engineers his way into the bank as an IT guy and plugs-in the USB drive. Below are screenshots of the well-crafted ransomware message.
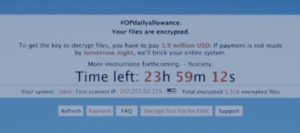
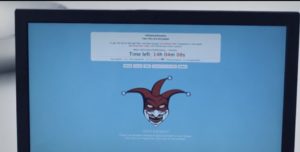
The message says that a payment of USD 5.9 million is require if the bank wants to recover the data. It then mentions the deadline of 24 hours within which the payment has to be done else the virus will brick all the computers in the network.
While this is not the first television adaptation of a computer virus but it’s better than most. Watch the show and watch out for ransomware.
Do share your thoughts on ransomware as well as Mr. Robot.
Uday Mittal is a cybersecurity professional with rich working experience working with various industries including telecom, publishing, consulting and finance. He holds internationally recognized certifications such as CRTP, OSCE, OSCP, CISSP, CISA, CISM, CRISC among others. He speaks on cybersecurity awareness, offensive security research etc. and has authored various articles on topics related to cyber security and software development for a leading magazine on open source software.
