This post is part of our course Adversary Emulation 101: Mimicking a real-world cyber attack.
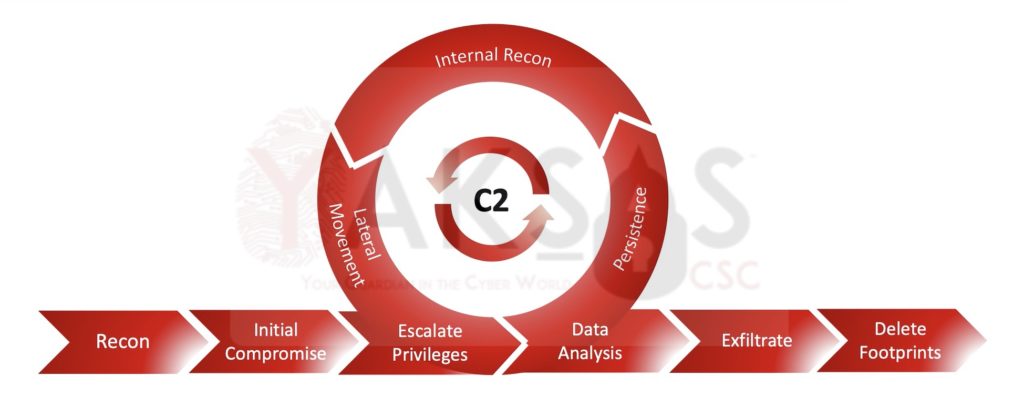
The lifecycle consisted of following phases, with phases 3-6 being cyclic in nature:
- Recon (Information Gathering) – In this phase, publicly available information (website, company profile, social media pages, employee profiles etc.) is gathered about the target organization.
- Initial Compromise (Foothold) – In this phase, information from Recon phase is analysed to identify and exploit a vulnerability or launch a phishing attack that helps in establishing a foothold within the target network.
- Privilege Escalation – In this phase, the attacker attempts to escalate privileges to an administrator (Windows) or root (Linux) account on the compromised host. Usually, this is done each time a new host is compromised.
- Establishing Persistence – In this phase, the attacker installs a persistence mechanism (usually a Command and Control (C2) agent) to maintain presence in the target network. This enables the attacker to communicate with compromised hosts without having to exploit it again in case the original connection dies out. Usually, this is done each time a new host is compromised.
- Internal Recon – In this phase, the attacker leverages the compromised host to gather information about the internal network. Usually, this is done each time a new host is compromised and is thought to have access to more resources. For example, if an attacker compromises an Active Directory domain joined machine, they can use that machine to enumerate the Active Directory network.
- Lateral Movement – In this phase, the attacker tries to expand their access by compromising new hosts within the target network. The information collected during Internal Recon phase is leveraged here.
- Data Analysis – As new hosts are compromised, the attacker scans each of them for interesting information (employee records, financial statements, PII, credit card information, customer databases etc.).
- Exfiltration – Anything that the attacker deems useful is pulled out and downloaded onto the attacker machine (or their chosen location).
- Deleting footprints – Once the attacker has achieved their objective, they delete all files, logs, emails etc. created by them during the exercise to hide their presence.
Featured Image Source: Freepik.com
Uday Mittal is a cybersecurity professional with rich working experience working with various industries including telecom, publishing, consulting and finance. He holds internationally recognized certifications such as CRTP, OSCE, OSCP, CISSP, CISA, CISM, CRISC among others. He speaks on cybersecurity awareness, offensive security research etc. and has authored various articles on topics related to cyber security and software development for a leading magazine on open source software.
