Whether it’s cricket ground or battle-ground, things always heat up when the two sides are India and Pakistan. Off late, they’ve found a new frontier to battle, the cyber-ground. Both the nations have been in the state of unofficial cyber-warfare since 2010 and it doesn’t seem to end any time soon.
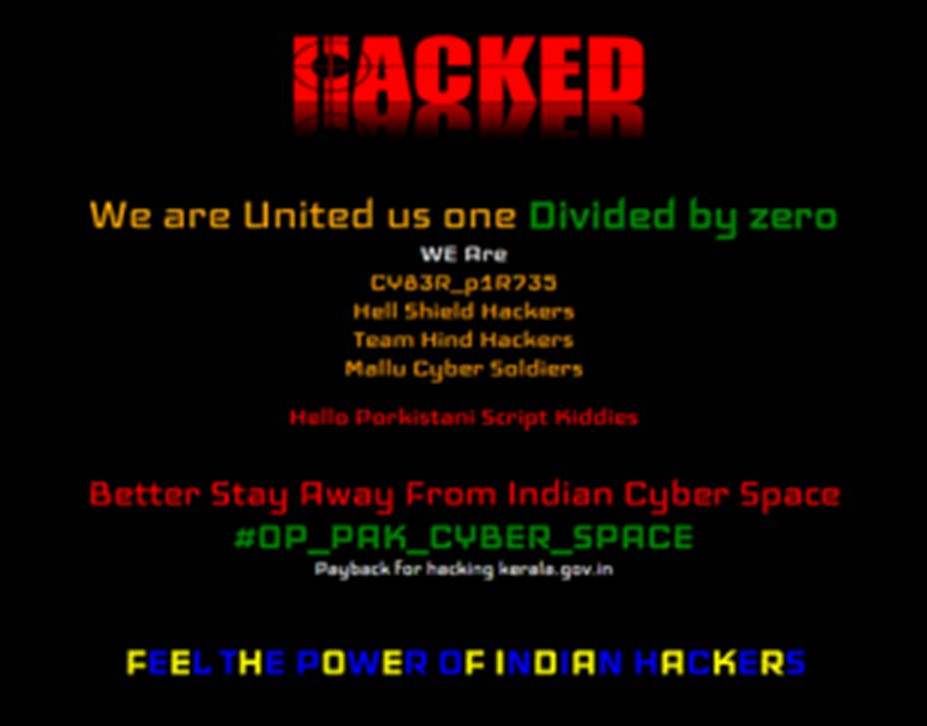
Yesterday, a Pakistani hacker by the name of Faisal Afzal (Faizal 1337) defaced Kerala government’s website kerala.gov.in. The hacked website displayed a burning Indian flag along with the message, ‘Pakistan Zindabad’. Outraged by this, Indian hacktivist groups, collectively known as Anonymous India, decided to launch a payback operation named #OpPAKPayback. Through this operation they hacked, defaced and DDoSed over fifty Pakistani websites. A classic tit for tat.
As per the message displayed on defaced Pakistani websites, Anonymous India seems to include following hacktivist groups:
- cy83r_p1r4735
- Hell Shield Hackers
- Team Hind Hackers
- Mallu Cyber Soldiers
Uday Mittal is a cybersecurity professional with rich working experience working with various industries including telecom, publishing, consulting and finance. He holds internationally recognized certifications such as CRTP, OSCE, OSCP, CISSP, CISA, CISM, CRISC among others. He speaks on cybersecurity awareness, offensive security research etc. and has authored various articles on topics related to cyber security and software development for a leading magazine on open source software.
