Assignment Task:
- Take up 3 shellcodes from Shell-Storm and create polymorphic versions of them to beat pattern matching
- The polymorphic versions cannot be larger 150% of the existing shellcode
Shellcode 1: shutdown -h now
Shell-Storm Link: http://shell-storm.org/shellcode/files/shellcode-876.php
The original shellcode was 56 bytes in size.
Link to original code:
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-1/shellcode-6-1-orig.nasm
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-1/run-shellcode-6-1-orig.c
Techniques used to modify this shellcode:
- Kept only first Xor instruction and replaced the remaining with mov instruction
- Added NOP in between PUSH instructions to break the pattern
- Changed first three PUSH EAX instructions to PUSH EDX
The length of modified shellcode is 61 bytes and it worked perfectly as can be seen below:
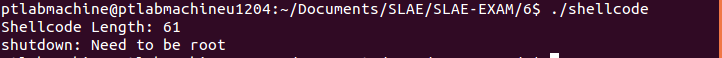
Link to polymorphic shellcode:
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-1/shellcode-6-1-poly.nasm
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-1/run-shellcode-6-1-poly.c
Shellcode 2: adds a root user no-passwd to /etc/passw
Shell-Storm Link: http://shell-storm.org/shellcode/files/shellcode-548.php
The original shellcode was 83 bytes in size.
Link to original code:
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-2/shellcode-6-2-orig.nasm
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-2/run-shellcode-6-2-orig.c
Techniques used to modify this shellcode:
- Replaced certain Xor instructions with MOV instruction after the initial Xoring
- Added NOP in between PUSH instructions to break the pattern
- Replaced certain PUSH instructions with add or subtract routine
- Add additional XOR instruction, wherever necessary
- Replaced the username bob with csc
The length of modified shellcode is 105 bytes and it worked perfectly as can be seen below:
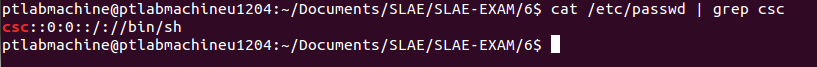
Link to polymorphic shellcode:
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-2/shellcode-6-2-poly.nasm
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-2/run-shellcode-6-2-poly.c
Shellcode 3: linux x86 nc -lvve/bin/sh -p13377
Shell-Storm Link: http://shell-storm.org/shellcode/files/shellcode-804.php
The original shellcode was 64 bytes in size.
Link to original code:
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-3/shellcode-6-3-orig.nasm
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-3/run-shellcode-6-3-orig.c
Techniques used to modify this shellcode:
- Replaced certain Xor instructions with MOV instruction after the initial Xoring
- Replaced certain PUSH instructions with add or subtract routine
- Add XOR instruction, wherever necessary
- Changed the binding port to 2698
The length of modified shellcode is 77 bytes and it worked perfectly as can be seen below:
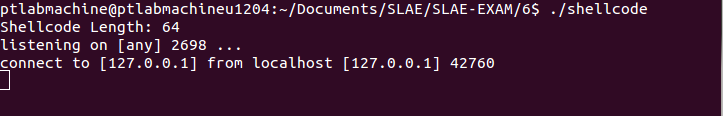
Link to polymorphic shellcode:
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-3/shellcode-6-3-poly.nasm
- https://github.com/yaksas443/SLAE/blob/master/Assignment%206/6-3/run-shellcode-6-3-poly.c
Assignment Github Link: Assignment 6
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
https://www.pentesteracademy.com/course?id=3
Student ID: SLAE-897
Uday Mittal is a cybersecurity professional with rich working experience working with various industries including telecom, publishing, consulting and finance. He holds internationally recognized certifications such as CRTP, OSCE, OSCP, CISSP, CISA, CISM, CRISC among others. He speaks on cybersecurity awareness, offensive security research etc. and has authored various articles on topics related to cyber security and software development for a leading magazine on open source software.
