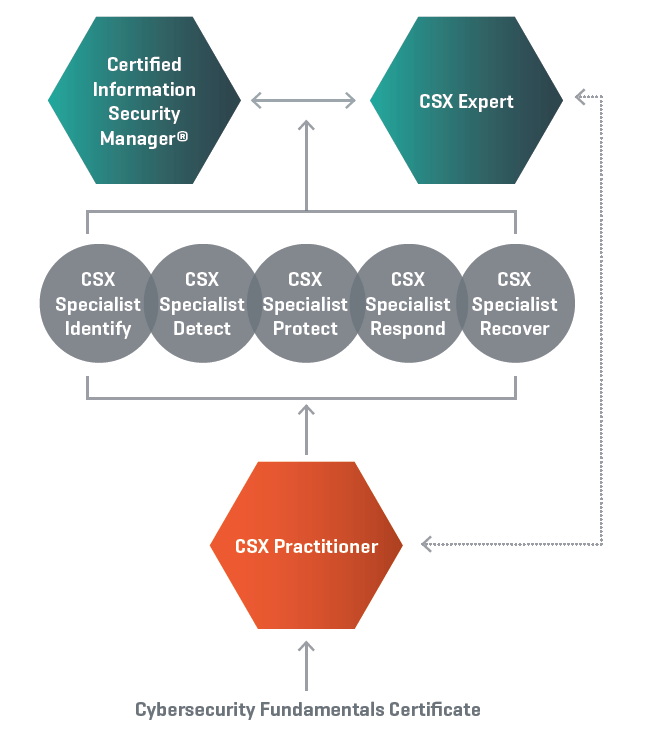
Last year, ISACA launched a new series of certifications, focused on Cyber Security, called CyberSecurity Nexus (CSX) Certifications. This series contains a total of eight certifications leading to either CSX Expert or CISM.
Image Source: Isaca.org
CSX Fundamentals is the first certification in this series. I started my certification path with it and would like to share the experience (as much as I can without violating the NDA) . I hope that those of you who are currently preparing for it or wish to pursue it in future may find something to take away from this article. For the benefit of the readers who have just started their careers in or are planning to enter the Cyber Security field I’ll start with a brief introduction of the Certification.
About the CSX Fundamentals Certification
It’s an entry level certification, ideal for college/ university students and recent graduates, those new to the field, as well as those looking to change careers. The subject matter provides an eagle’s eye vision of the field and introduces core concepts, though not in much detail. The Certificate is aligned with the National Institute of Standards and Technology (NIST) National Initiative for Cybersecurity Education (NICE), which is compatible with global cyber security issues, activities and job roles. It is also aligned with the Skills Framework for the Information Age (SFIA). You can read more about it here.
What does it cover?
Curriculum for CSX Fundamentals is divided into following five key areas:
- Cyber security concepts.
- Cyber security architecture principles.
- Cyber security of networks, systems, applications and data.
- Incident response
- The security implications of the adoption of emerging technologies.
While it’s important to understand the knowledge statements and the objective they serve, one doesn’t need to mug them.
How to prepare for the exam?
The only thing you need to pass the exam is ISACA’s CSX Cybersecurity Fundamentals Study Guide . It’s around 192 pages priced at $45 (INR 2,835) for members and $55 (INR 3,465) for non-members. The study guide comes in two versions, PDF and book. Unfortunately, a comprehensive practice question database is not available. However, the study guide includes ample number of questions to give the candidates a taste of the exam. A practice quiz, containing 25 questions, for self-assessment is also available. It is essential to have a good understanding of concepts in order to clear the exam, mugging up won’t help. Additional resource can be accessed here.
What’s the exam like?
The Cybersecurity Fundamentals Certificate exam is an online, closed-book, remotely-proctored exam. Candidates can take the exam in privacy of their home. It is a two hours examination in which candidates have to answer 75 multiple-choice questions. Minimum passing score is 65%
The exam fee may vary from $195 (INR 12,285) for non-members to $185 (INR 11,655) for members. This price is inclusive of the CSX Cybersecurity Fundamentals Study Guide. Candidates can start the exam registration process from here (ISACA account required).
While taking the exam, candidates will be monitored by a proctor via the webcam. For this purpose, ISACA requires them to install a plugin on their system. It is recommended that candidates run this System Requirements check prior to taking the exam. In case, the system doesn’t meet these requirements, candidates will have to arrange for another system. Candidates should also keep Skype installed on their system, as a backup if the plugin doesn’t work. Detailed hardware and software requirements can be found here.
What’s next after clearing the exam?
There are no experience requirements in order to claim the certification. Therefore, upon clearing the exam candidates earn the CSX Fundamentals certificate. There no maintenance requirements as well.
—
If I have left out anything or if readers have any additional queries please leave them in the comments below. Please note that questions regarding sharing and distribution of pre-owned material will not be entertained as it amounts to piracy.
Uday Mittal is a cybersecurity professional with rich working experience working with various industries including telecom, publishing, consulting and finance. He holds internationally recognized certifications such as CRTP, OSCE, OSCP, CISSP, CISA, CISM, CRISC among others. He speaks on cybersecurity awareness, offensive security research etc. and has authored various articles on topics related to cyber security and software development for a leading magazine on open source software.